Exploiting Router Authentication through Web Interface
The “iBall Baton 150M Wireless Router Authentication Bypass Vulnerability” is the one I found when I was studying in the college. I was simply browsing the router pages to see if there is any way to get authorized page without username/password. Somehow I noticed a web request is sending to a .cgi page. I guessed there is some page in cgi extension instead of html. So I tried an existing known page password.html with password.cgi. Luckily I got the authentication bypassed and showed password reset page. Later I identified all existing pages can be accessed in this way without username/password. While checking the source code of password reset page, I found the passwords of each login accounts in clear text! Clearly it is a critical vulnerability iBall router.
Routers such as D-Link , Linksys etc. whose web interface uses CGI scripts. We can easily access and change these routers configuration bypassing authentication. CGI is one method by which a web server can obtain data from (or send data to) databases, documents, and other programs, and present that data to viewers via the web. The authentication bypass vulnerability is powerful as anyone can change router configuration, such as changing passwords, resetting router etc. through any web browser. The steps are mentioned below:
First we need the router IP, which is usually IPV4 Default Gateway IP. We can find this using ipconfig /all command from cmd or checking details of network adapter connected to network from Network and Sharing Center.
Most common default router IPs are 192.168.0.1, 192.168.1.1 etc. Suppose the router IP is 192.168.1.1, we change the URL format of any web page to ends with .cgi.
Ie, we change
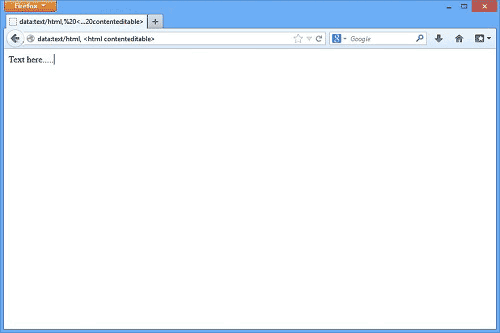
http://192.168.1.1/password.html
to
http://192.168.1.1/password.cgi
Watch this video demonstration for more details. This video shows mainly:
- Accessing router configuration without username and password
- Finding usernames and passwords which are hidden inside page source
Watch video: https://youtu.be/8GZg1IuSfCs
Some other pages we can directly access like this are:
http://192.168.1.1/upload.cgi
http://192.168.1.1/resetrouter.cgi
http://192.168.1.1/pppoe.cgi
http://192.168.1.1/info.cgi
Identified and Reported by
Gem George


Recent Comments